System Security Measures For Software And Data Management
It is quite unfortunate to see many businesses still using old software and operating system. 10 data security measures every project manager should implement.
 Cover Your Business Risks With Advanced Cyber Security
Cover Your Business Risks With Advanced Cyber Security
system security measures for software and data management is important information accompanied by photo and HD pictures sourced from all websites in the world. Download this image for free in High-Definition resolution the choice "download button" below. If you do not find the exact resolution you are looking for, then go for a native or higher resolution.
Don't forget to bookmark system security measures for software and data management using Ctrl + D (PC) or Command + D (macos). If you are using mobile phone, you could also use menu drawer from browser. Whether it's Windows, Mac, iOs or Android, you will be able to download the images using download button.
When we talk about implementing basic security measures one could think and what are those and if that question would be asked it would be a very very difficult question to answer.

System security measures for software and data management. Data security is an essential aspect of it for organizations of every size and type. These data security measures define the minimum security requirements that must be applied to the data types defined in the reference for data and system classification. Security and control in management information system 1.
If you are a system administrator an it security manager in your company or just a regular information. Technical and organizational data security measures 2017v1 page 5 of 7 requirements driven definition of the authorization scheme and access rights as well as their monitoring and logging. Security and control by satya prakash joshi 2.
Information systems are composed in three main portions hardware software and communications with the purpose to help identify and apply information security industry standards as mechanisms of protection and prevention at. Security and control computer system play such a critical role in business government and daily life that firms need to make security and control a top priority. Data handling security measures.
Data security refers to protective digital privacy measures that are applied to prevent unauthorized access to computers databases and websites. In a time when data privacy and security matters personal information controller and personal information processors are obliged to implement strong reasonable and appropriate organizational physical and technical security measures for the protection of the personal information that they process. Regular review of accounts and privileges typically every 3 6 months depending on the.
Or qualities ie confidentiality integrity and availability cia. Computer security cybersecurity or information technology security it security is the protection of computer systems from the theft of or damage to their hardware software or electronic data as well as from the disruption or misdirection of the services they provide. Here are 10 data security measures that every project manager should take to ensure foolproof security of data.
Some data elements such as credit card numbers and patient health records have additional security requirements defined in external standards. Data security also protects data from corruption. Take software application security training course by technology and management training courses and seminars tonex software security training incorporates numerous in class exercises including hands on activities contextual analyses and workshop.
 Google Infrastructure Security Design Overview Solutions
Google Infrastructure Security Design Overview Solutions
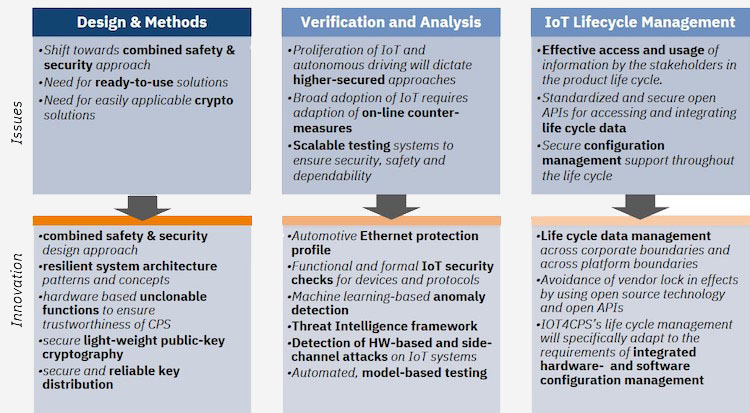 Safety Security Design And Methods Iot4cps
Safety Security Design And Methods Iot4cps
 Pim Data Governance Data Quality Management Agility
Pim Data Governance Data Quality Management Agility
 Data Protection Software Otris Software Ag
Data Protection Software Otris Software Ag
 Database Security Authorization Encryption Ppt Video
Database Security Authorization Encryption Ppt Video

 10 Types Of Application Security Testing Tools When And How
10 Types Of Application Security Testing Tools When And How

 Control Engineering Six Iot Implementation Challenges And
Control Engineering Six Iot Implementation Challenges And


0 Response to "System Security Measures For Software And Data Management"
Post a Comment